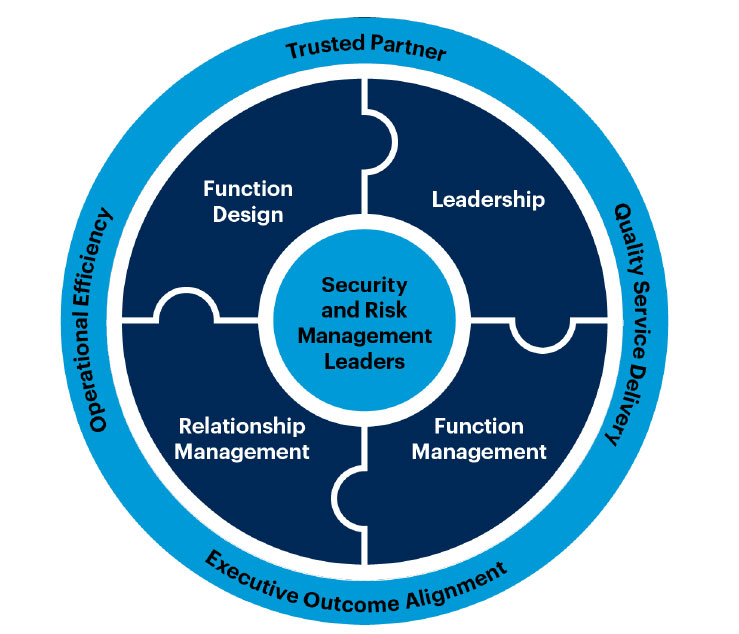
Report By Gartner As organizations go full in with digital initiatives, security and risk management leaders must help the business actualize value in an increasingly distributed risk decision-making environment built for real-time adaptability and resilience through risk-based programs. The Gartner report helps organizations design, develop, govern and manage their specific security and risk management (SRM) […]
Security researchers at Sansec (https://sansec.io/research/cronrat) have found a new stealth attack that targets Linux servers and uses a non-existent calendar day to stay off the radar. This Remote Access Trojan (RAT) masks the actions of the attack by using the date February 31 and targets Linux-based web stores to trigger online payment skimmer threats. The […]
OpenSSH has joined the high-stakes fight to protect data from quantum computers. The latest version of the widely used encryption and connectivity tool has been fitted with new features to prevent “capture now, decrypt later” attacks linked to advancements in quantum computing. Security experts warn that advanced threat actors are already stealing and storing encrypted […]
The latest Chrome security update started rolling out with patches for 11 vulnerabilities. Ten of the addressed vulnerabilities were reported by external researchers. Of these, eight are rated “high severity” and two “medium severity.” Six of the externally reported security holes are use-after-free bugs, which in some cases can lead to code execution. Five of […]
Multi-factor authentication (MFA) was once a foreign terminology, but today, with the myriad of hacks and data breaches dominating headlines, it’s fair to say that most individuals now see MFA as a no-brainer – for now. When thinking about MFA, both companies and consumers alike consider it to be a safer, more secure option. And […]
Building an effective cyber security program in today’s environment is more challenging than ever. A growing amount of connected devices paired with an IT network and perimeter that is more decentralized than ever due to cloud functionality and remote work, has resulted in organizations struggling to keep security operations maintained efficiently. All this, on top […]
In the wake of the global pandemic, organizations of all types and sizes have pivoted to cloud resources to accommodate the rise of distributed, remote work. Businesses have never been more reliant on the cloud than they are today. The proof is in the remarkable growth we’re seeing in cloud spending and cloud software-as-a-service (SaaS) […]
Last year was a challenging year for IT teams, and tech workers will continue to feel the mounting burden of maintaining business continuity moving forward. In the early part of 2020, IT teams were stressed to the brink as they scrambled to help their organizations adapt to the realities of the COVID-19 pandemic. Digital transformation […]
Magecart has definitely gathered mainstream media attention over the last couple of years. Perhaps it’s the high-profile nature of many of their targets (British Airways, Forbes, Equifax, Macy’s) to name but a few. Magecart is best described as a cybercrime syndicate that specialises in cyberattacks involving digital credit card theft, by skimming online payment forms. […]