Security and Risk Management Leaders Primer
Report By Gartner
As organizations go full in with digital initiatives, security and risk management leaders must help the business actualize value in an increasingly distributed risk decision-making environment built for real-time adaptability and resilience through risk-based programs.
The Gartner report helps organizations design, develop, govern and manage their specific security and risk management (SRM) programs to provide and protect their value.
In addition to security and risk management leaders and business leaders, other IT roles involved in this initiative are:
- Chief information officers
- Infrastructure and operations leaders
- Enterprise architecture and technology innovation leaders
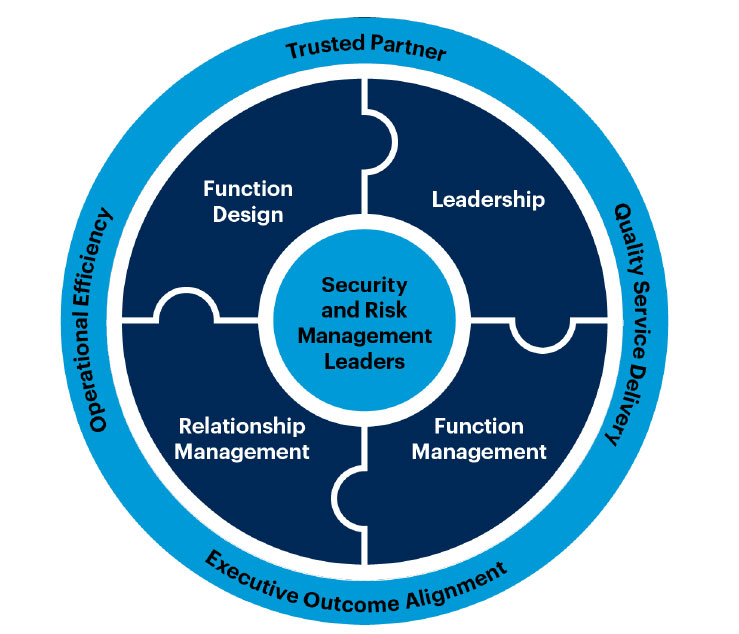
The topics we cover include:
- Function Design: The organizational structures that work best for the SRM programs; how to design the appropriate scope, function design and architecture; vision for the program; emerging trends that affect the roles; and why the roles are increasingly critical.
- Function Management: How to manage the protection of business operations and related resources. This includes facilities, information technology, personnel, equipment and third parties. This activity requires sourcing and prioritizing function resources.
- Leadership: SRM leadership is about effective functional management, quality customer service, providing scaled governance and influencing positive employee behaviours. Reaching these desired outcomes entails having a vision and strategy for reaching business objectives.
- Relationship Management: Understanding internal and external stakeholder relationships and their communication and reporting needs; establishing strong communication and reporting practices for various constituencies (for example, peers and management, CxO/board); and establishing specific SRM program workforce awareness and training best practices.
Analysis
The past year showed that in disruption lies opportunity, even if it also proved how painful turmoil can be. Mature organizations have been exploring a more resilient, adaptable form of business to ensure they drive toward desired outcomes in both calm times and turmoil.
In this model, leaders leverage digital investments and accelerate digital strategies in an organization that is architected for real-time adaptability and resilience in the face of uncertainty by pursuing highly modular solutions.
SRM leaders must help business leaders actualize value through risk-based programs that ensure composable trust and resilience in decentralized risk decision-making organizations.
SRM leaders are responsible for ensuring that risk-related processes, controls and technologies in many different domains address business-critical enterprise risks. The roles covered as part of Gartner’s SRM research are:
- Chief information security officer
- Information/IT security management leader
- IT risk leader
- Business continuity management program leader
- Privacy/data protection officer
- Identity and access management leader
- Chief security officer
Topics
The principles of composable business — modularity, orchestration, autonomy and discovery — allow for extended capabilities and continuous adaptability.
In this context, Gartner’s research provides the knowledge that SRM leaders need to advise and influence senior business leaders. This guidance enables business leaders to make the right decisions, positions the organization to create value and helps achieve the defensibility of strategic decisions. Governance, communications, awareness, process and resources are key to success for SRM leaders, but they also align SRM programs with the business itself, becoming part of and responding to the same imperatives.
Gartner’s research in this area addresses the following topics:
Function Design
SRM leaders often desire to know where they should ideally report and what activities they should own. While there is not one ideal function design, there are common challenges and trends that should guide how SRM leaders build their programs.
In the past few years, the boundaries of SRM have grown increasingly blurry. Technologists and security professionals are hired in greater numbers directly into the business. In 2020, 44% of digital delivery team leaders were located outside of IT, according to Gartner’s research on cyber judgment.
More security happening outside of traditional channels means SRM leaders have decreased visibility into the quality of security and risk processes; they also must often work through influence to ensure the right controls and security practices are in place. Finally, as SRM risk domains become a core component of practically every business process and objective, the scope of the function may become an umbrella for a variety of security disciplines.
SRM leaders should:
- Design an operating model that takes into account the enterprise culture and maturity.
- Have explicit conversations with senior leadership about their function’s scope and objectives.
- Assess the effectiveness of not just their immediate teams, but also of the cybersecurity professionals who report directly to the business.
Questions Your Peers Are Asking
- How can my function show value to the enterprise, rather than just being perceived as a cost center?
- How do I organize accountability and reporting relationships for the program?
- What are the key practices for the program?
Function Management
As SRM programs expand beyond their previously defined borders, SRM leaders maintain ownership of their traditional management activities, while stewarding the organization to attain security and risk goals, and the talent, skills, knowledge and capabilities required to execute against core business objectives.
A few key challenges to successful functional management persist. First, current governance processes are increasingly becoming archaic and too inflexible for iterative and distributed digital workflows.
Second, some SRM programs such as cybersecurity don’t sufficiently account for the rapid spread of technical expertise outside of IT, mostly focusing on security talent management within their borders.
Finally, SRM leaders still struggle to define meaningful program performance metrics that can be used to justify budget spending.
SRM leaders should:
- Develop and maintain the policy as a process, asking for and implementing feedback from those expected to adhere to it.
- Define and plan the skills, knowledge and capabilities needed most by the enterprise, and assist different parts of the business in bringing them in.
- Work with senior leadership to define objectives that their programs support.
Questions Your Peers Are Asking
- How do I develop and maintain effective governance across the organization?
- What do effective policies, standards and guidelines look like?
- How can I use key metrics and indicators to measure the effectiveness of individual controls, as well as the whole program?
- How do I plan and justify budgets?
- How do I recruit and train staff?
- How do I mature the program?
Leadership
Personal effectiveness of SRM leaders has been synonymous with functional effectiveness for far too long. Our research shows that not only are they not the same, but without this differentiation, functional maturity and the professional growth of SRM leaders eventually hit a point of diminishing returns.
SRM leaders are experiencing a rapidly increasing scope of responsibilities, greater visibility and increased scrutiny of their performance as leaders and their decisions. They are feeling the weight of their added responsibilities; Gartner’s 2020 survey on CISO effectiveness found that only 19% of CISOs feel that they effectively manage stress at work.
SRM leaders should:
- Clearly define scope of responsibilities, focusing on comparative advantage.
- Help the organization balance the need to facilitate business outcomes against the need to manage risk holistically.
- Assess and transform SRM programs, as well as themselves, to become digital business enablers.
Questions Your Peers Are Asking
- How do I enable the business to meet its objectives?
- What does a mature security strategy planning document look like?
- What are the key behaviors and competencies that make up an effective leader?
Relationship Management
Relationship management is a core responsibility of SRM leaders, as risk decision making becomes more distributed, touching all parts of the enterprise. SRM leaders must form stronger relationships with stakeholders outside of IT, while maintaining bonds with the IT community, crafting effective communications plans for different audiences.
SRM leaders still tend to prioritize stakeholders inside of the formal IT function, devoting disproportionately more time interacting with individuals who have traditionally managed technology. When they do branch out, they do so with messages not tailored for the audience that often fail to resonate.
SRM leaders should:
- Prioritize building relationships with stakeholders who are in areas of the business, while maintaining relationships with IT stakeholders for efficiency.
- Assess the enterprise constituencies and craft targeted messages.
- Recognize that communication alone does not help build the case. Show value and deliver services that help the organization achieve its objectives.
Questions Your Peers Are Asking
- How do I successfully communicate with various internal and external stakeholders?
- How do I educate the board of directors/senior executives on the challenges and risks of the program?
- How do I align security services/outcomes with business value?
Ref: https://www.gartner.com/en/doc/736848-security-and-risk-management-leaders-primer-for-2021